Welcome to my Website
Hi, I’m Muhammad Ahsan
a
AI Engineer
cyber security expert
Data Analyst
Web Developer
Versatile technologist with expertise in AI, data analysis, IoT, cybersecurity, and web development. Passionate about using technology to solve complex problems and create breakthroughs.
DOWNLOAD MY Data Analyst CV
DOWNLOAD MY Cyber security CV
find with me
best skill on

4+ Years of Experience
My Resume
Education Quality
BS Artificial intelligence
University of Management & Technology (2019 – 2023)
1st division
The training provided by universities in order to prepare people to work in various sectors of the economy or areas of culture.
FSC – Science
Cadet college kallar kahar (2017 – 2019)
1st division
Higher education is tertiary education leading to award of an academic degree. Higher education, also called post-secondary education.
Secondary School Education
Cadet college kallar kahar (2016 – 2017)
1st division
Secondary education or post-primary education covers two phases on the International Standard Classification of Education scale.
Click here to view my all Licenses & certifications
Licenses & certifications
Google Advanced Data Analytics Professional Certificate
Skills: Microsoft Power BI · Tableau · Data Analysis · Python (Programming Language)
Python 3 Programming Specialization
University of Michigan
Skills: Python (Programming Language)
Data Collection and Processing with Python
University of Michigan
Skills: Data Science · Python (Programming Language)
Foundations of Data ScienceFoundations of Data Science
Skills: Data Science · Data Analysis
Fundamentals of Visualization with Tableau
University of California, Davis
Skills: Data Visualization
Get Started with Python
University of Michigan
Skills: Python (Programming Language)
Go Beyond the Numbers: Translate Data into Insights
Skills: Data Visualization · Data Science · Data Analysis · Python (Programming Language)
Google Advanced Data Analytics Capstone
Skills: Machine Learning · Visualization · Data Visualization · Data Science · Deep Learning · Statistical Data Analysis · Data Analysis · Python (Programming Language) · Exploratory Data Analysis
Machine Learning with ChatGPT: Image Classification Model
Coursera
Skills: Machine Learning · ChatGPT
Python Basics
University of Michigan
Skills: Python (Programming Language)
Python Classes and Inheritance
University of Michigan
Skills: Python (Programming Language)
Python Functions, Files, and Dictionaries
University of Michigan
Skills: Python (Programming Language)
Python Project: pillow, tesseract, and opencv
University of Michigan
Skills: Python (Programming Language)
Regression Analysis: Simplify Complex Data Relationships
Skills: Data Visualization · Data Science · Statistical Data Analysis · Data Analysis · Python (Programming Language) · Exploratory Data Analysis
The Nuts and Bolts of Machine Learning
Skills: Machine Learning · Data Visualization · Data Science · Deep Learning · Statistical Data Analysis · Data Analysis · Python (Programming Language) · Exploratory Data Analysis
The Power of Statistics
Skills: Data Science · Statistical Data Analysis · Data Analysis · Python (Programming Language) · Exploratory Data Analysis
What is Data Science?
IBM
Skills: Data Science
Build and Sell APIs The Right Way
LearnWithHasan
skills: Build and Sell APIs
Prompt Engineering From Zero To Scripting AI Work Flows
LearnWithHasan
skills: Prompt Engineering
Cyber Security (2019 – 2024)
Licenses & certifications
Ethical Hacking Essentials (EHE)
EC-Council
Skills: Cybersecurity · Ethical Hacking
Introduction to Cyber Security
TryHackMe
Skills: Web Application Security · Operating System Security · Network Security Testing · Digital Forensics · Security Operations · Introduction to Cyber Security
Pre Security
TryHackMe
Skills: Offensive Security · Defensive Security · Networking · LAN · OSI Model · Packets & Frames · Extending Your Network · Domain Name System (DNS) · Hypertext Transfer Protocol Secure (HTTPS) · How Websites Work · Linux · Linux Server · Kali Linux · Windows
Applied ChatGPT for Cybersecurity
Infosec
Skills: Cybersecurity · ChatGPT
Others (2019 – 2024)
Licenses & certifications
Business English Communication Skills
University of Washington
Skills: Communication · Social Media Communications · Voice Mail · Business Planning · Mobile Communications · Business Strategy · Organizing Meetings · Meeting Scheduling · Event Planning · Contract Negotiation · Public Speaking · Presentation Development · English · Business Communications · Strategic Communications · Audio Recording · Networking · Meeting Planning · Email · Microsoft PowerPoint · Negotiation · Presentations · Presentation Skills · Presentation Design · Business Meetings · Business English
Business English: Capstone Project
University of Washington
Skills: Communication · Business Planning · Business Strategy · Business Meetings · Meeting Scheduling · Event Planning · Contract Negotiation · Public Speaking · Presentation Development · English · Business Communications · Business English · Networking · Meeting Planning · Microsoft PowerPoint · Negotiation · Presentations · Presentation Skills · Presentation Design
Business English: Making Presentations
University of Washington
Skills: Business Planning · Slide Preparation · Public Speaking · Presentation Development · Business Communications · Microsoft PowerPoint · Presentations · Presentation Skills · Presentation Design
Business English: Meetings
University of Washington
Skills: Business Planning · Business Strategy · Business Meetings · Meeting Scheduling · Business Communications · Business English · Meeting Planning
Business English: Networking
University of Washington
Skills: Communication · Business Planning · Business Communications · Networking
Business English: Planning & Negotiating
University of Washington
Skills: Business Planning · Business Strategy · Event Planning · Contract Negotiation · Business Communications · Business English · Meeting Planning · Negotiation
WordPress (2019 – 2024)
Licenses & certifications
Build and Sell APIs The Right Way
LearnWithHasan
skills: Build and Sell APIs
How To Build a SAAS on WordPress
LearnWithHasan
skills: Build a SAAS on WordPress
Skill
Artificial Intelligence (AI)
95%
Python (Programming Language)
80%
Machine learning
70%
deep learning
60%
Data Visualization
80%
Data Analysis
90%
Data Science
65%
C++
70%
ChatGPT
80%
Exploratory Data Analysis
80%
Statistical Data Analysis
80%
SQL
65%
Microsoft Power BI
70%
Tableau.
70%
Business Communications
75%
Cybersecurity
Skill
Artificial Intelligence (AI)
95%
Python (Programming Language)
80%
Cybersecurity
75%
Ethical Hacking
85%
Radio Frequency & Communications
85%
TRY HACK ME
90%
ChatGPT
80%
Development
Skill
WordPress
95%
Web Development.
80%
HTML
75%
SOFTWARE
65%
CSS
70%
ChatGPT
80%
Job Experience
Web Developer
freelance web development – (2019 – present)
freelancer
Freelance web developer specializing in WordPress, and modern design principles for responsive, engaging websites.
Internet of Things(IOT)
internship – (2020 – 2021)
UMT
Gained practical IoT experience at UMT, developing and implementing connected device solutions
Features
About Me
Artificial Intelligence Engineer
use AI and machine learning techniques to develop applications and systems that can help organizations increase efficiency, cut costs, increase profits, and make better business decisions.
data analysis
I use Python and advanced data analysis techniques to uncover hidden patterns in your data.
cyber security experts
I safeguard your digital assets with strategic threat analysis and proactive security measures.
Web Development
We’ll handle everything from to web development process until it is time to make your project live.
Visit my projects and keep your feedback
My Projects
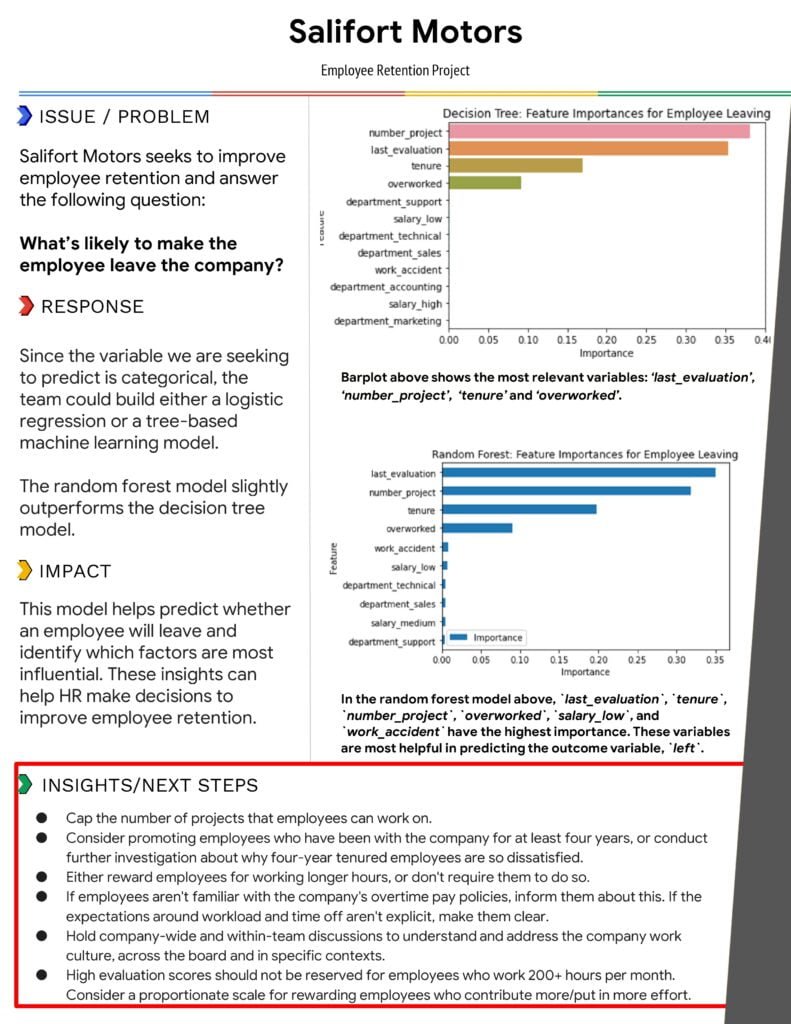
Salifort Motors data analysis
Salifort Motors data analysis
- service Data analysis
VIEW FULL PROJECT
Car Hacking System sing RTL SDR and Hack RF
Car Hacking System sing RTL SDR and Hack RF
- service Car Hacking System sing RTL SDR and Hack RF
Car Hacking System sing RTL SDR and Hack RF
IN This project we hack a car using an RTL SDR and Hack RF. Most RKEs operate at a frequency of 315 MHz for North American-made cars and at 433.92 MHz for European, Japanese, and Asian cars.
First, we use RTL SDR to check the frequency of the car key remote.
We use gqrx software for recording frequency.
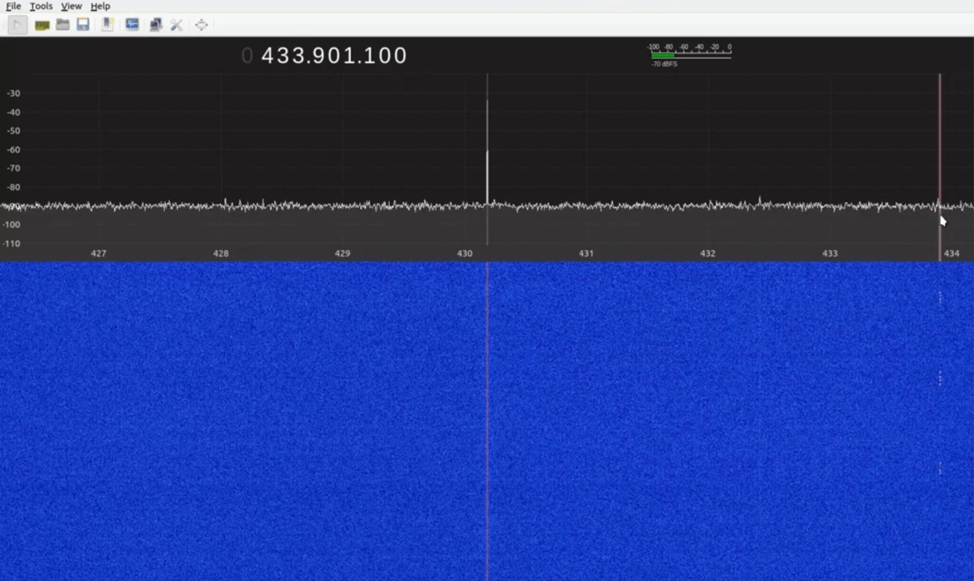
So we get the frequency of the car key remote and know we record this frequency and then we do a replay attack with the help of Hack rf.
For doing this replay attack we use a software
“Universal Radio Hacker “
The Universal Radio Hacker (URH) is a complete suite for wireless protocol investigation with native support for many common Software Defined Radios.
For installing this software we use these commands.
“git clone https://github.com/jopohl/urh.git”
But we use “Dragon OS” Dragon OS is an operating system with preinstalls all these software that hack RF and SDR needs so I do my attack on this operating system.
“ First we open terminal then type “urh” ”
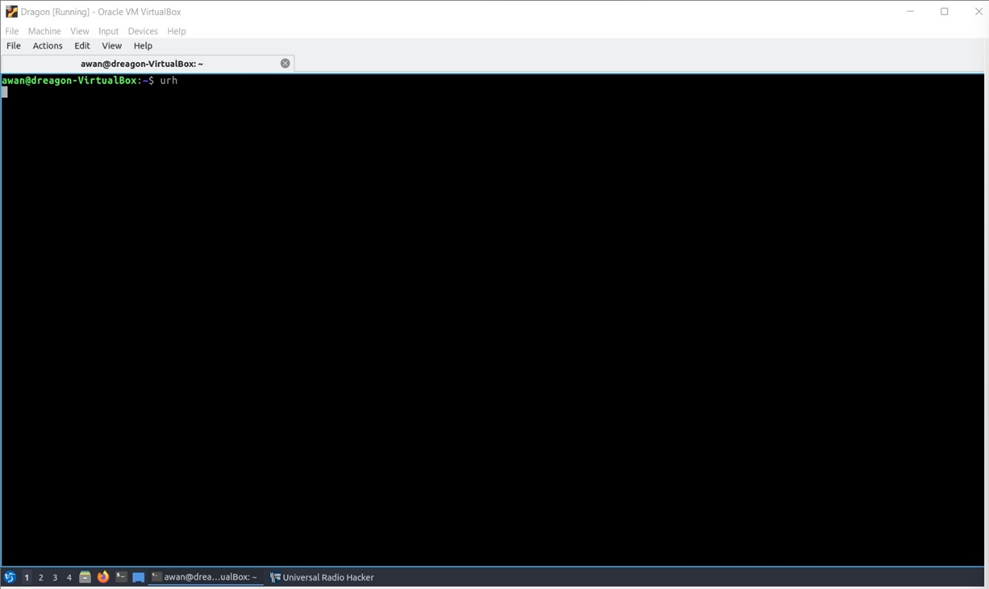
Then urh open in gui form
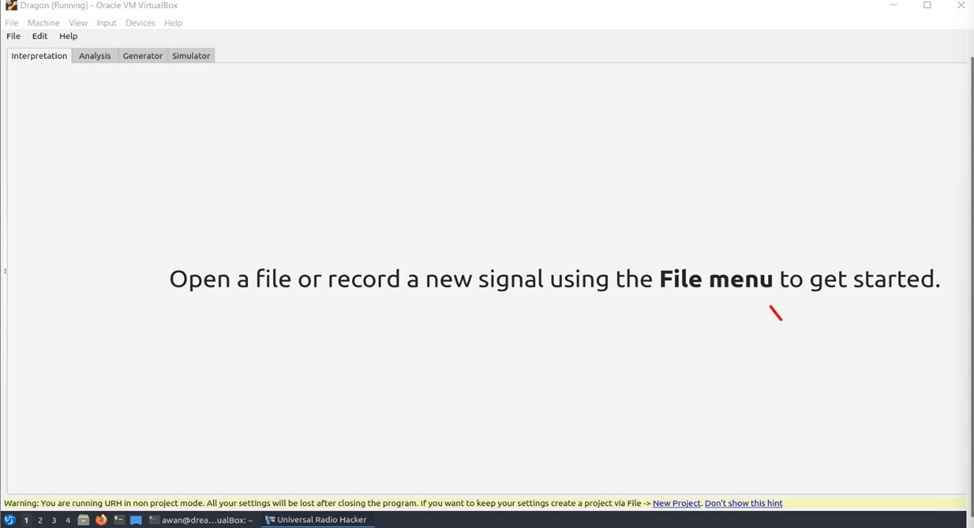
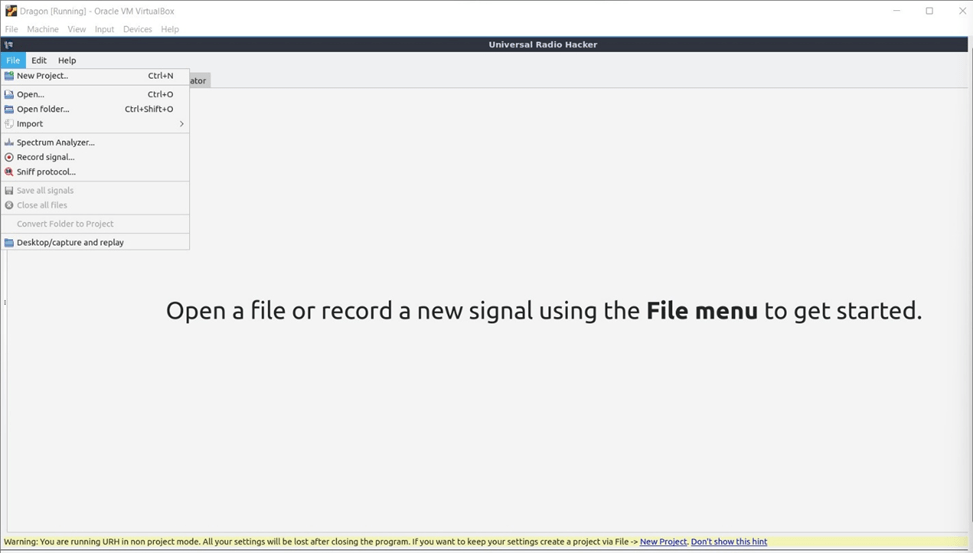
After that open file and create new project
We created a new project with name capture and replay.
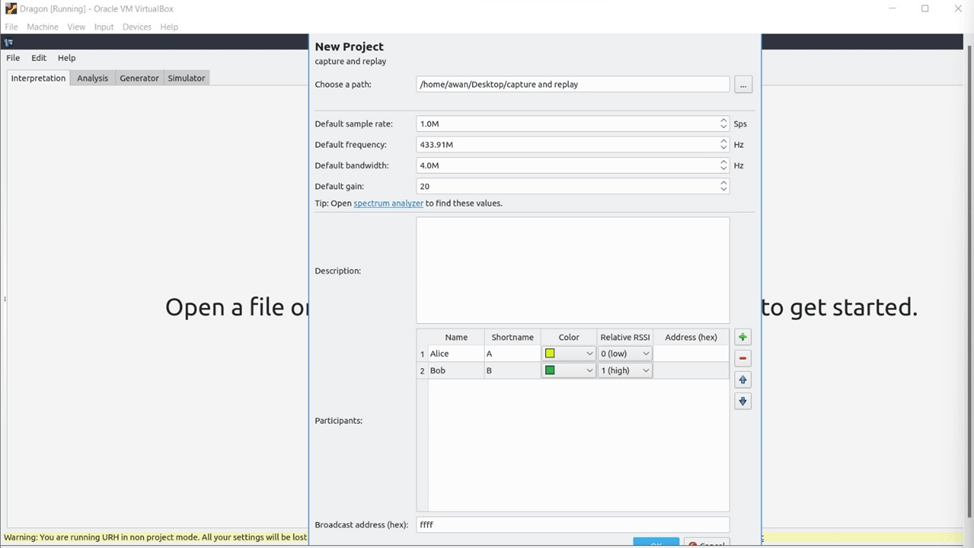
After creating a new project we set the frequency which we got before we set the frequency on 433.91M
And increase bandwidth to 4.0M.
To confirm frequency in this tool we open the “spectrum analyzer”
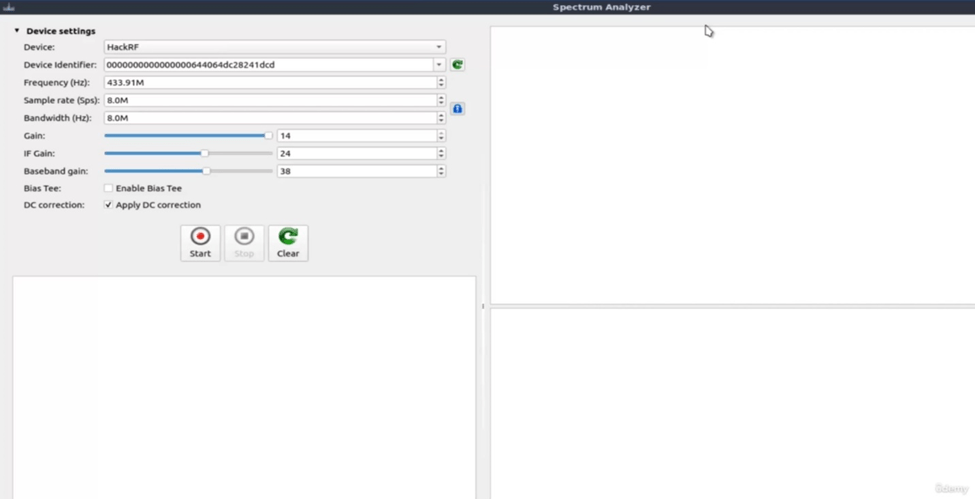
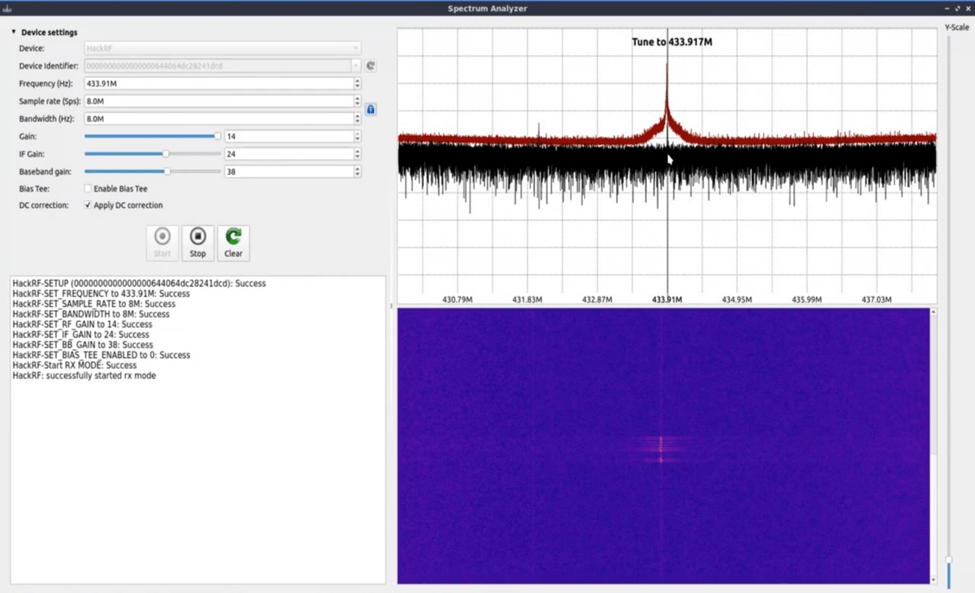
We set frequency and connect our hack RF and set bandwidth and gain and press start button.
so we confirmed our car key frequency on this tool.
After that we record this frequency.
For recording this frequency we open the record signal from the file option and record these car key frequencies for replay attack.
After opening the set frequency before we got and set all other settings and press start button.
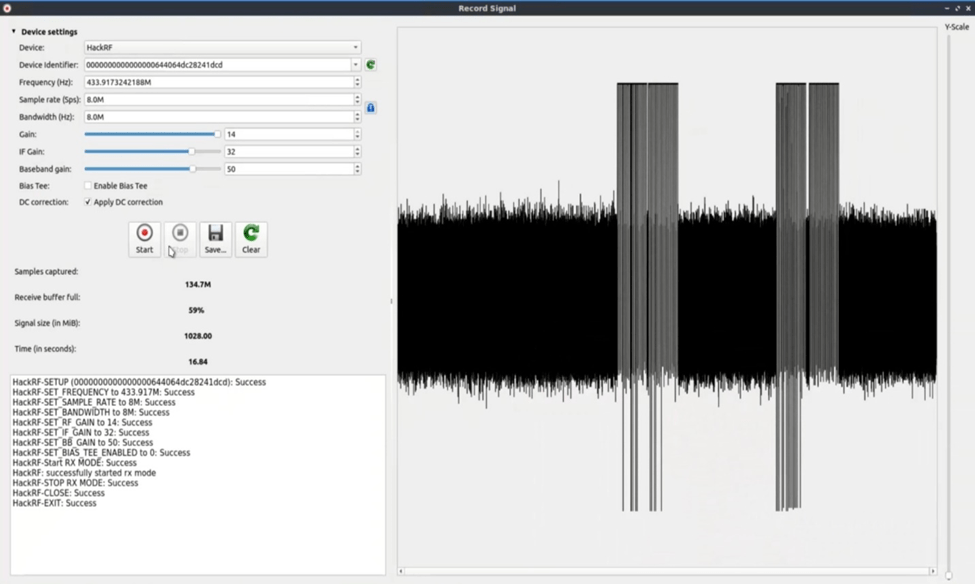
We recorded the frequency and then press the save button to save this frequency after that we do a replay attack.
For the replay attack open the saved file which we saved before and then putt the gain on zero and select our hack rf device and all other setting is same which we captured before.
Then just press the start button for replay attack
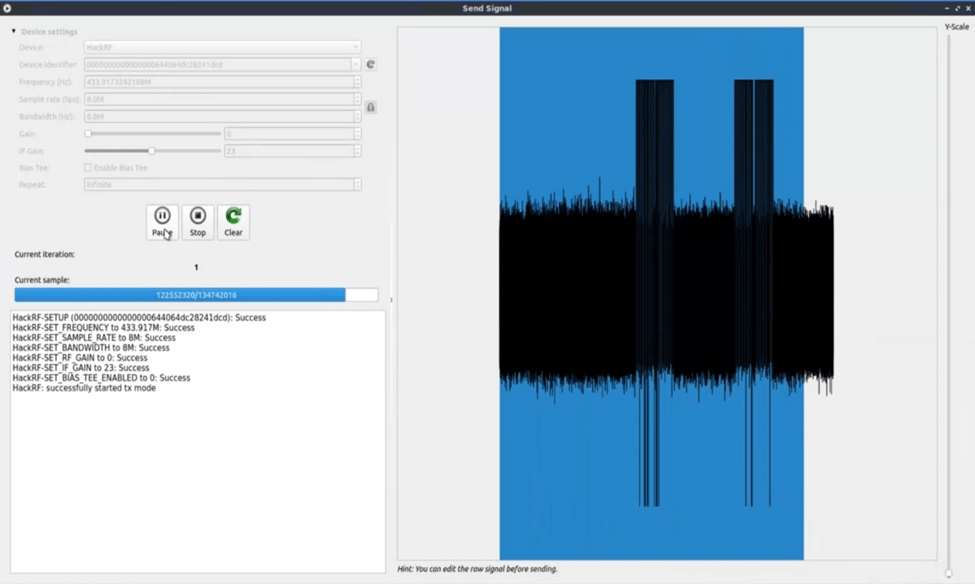
“KNOW our car opens without key just doing this replay attack with hack rf.”
Broadcast own signals with raspberry and jamming these signals.
Broadcast own signals with raspberry and jamming these signals.
Through a wide variety of jamming signals
- Service jamming signals
Broadcast own signals with raspberry and jamming these signals
IN this project we first do broadcasting our own signals using raspberry
First we install PiFmAdv in our raspberry

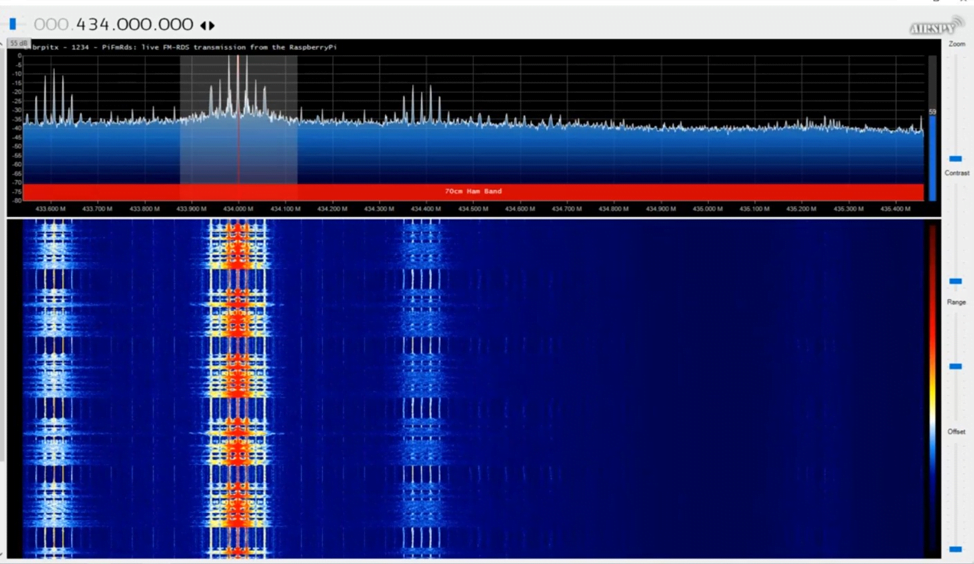
After that we use this command to broadcast signal on empty place where no signals before we get a place at 434.000.000
“sudo ./pi_fm_rds -freq 434.000 -audio sound.wav”
Then our signal is broadcosting which we see in below figure
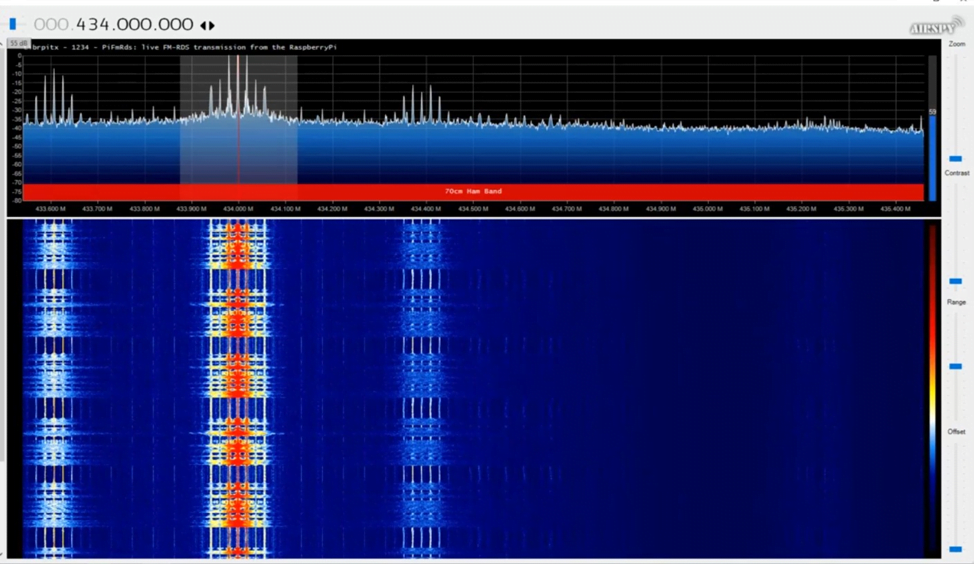
After broadcasting signals now we are going to jamm these Signals or doing distortion in signals
NOW we are going to jamm these signal .
First we install gr-osmosdr software for gamming signals
For installing this software we just type this command

Run this software just using this command
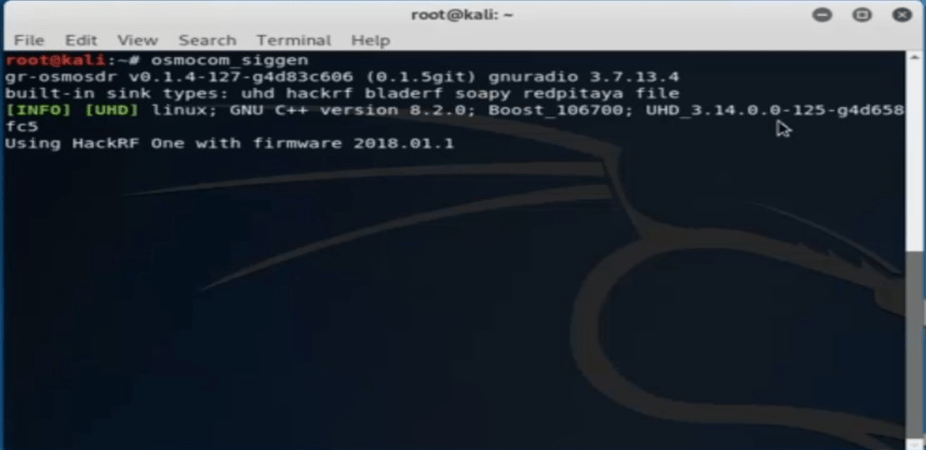
It runs in gui form
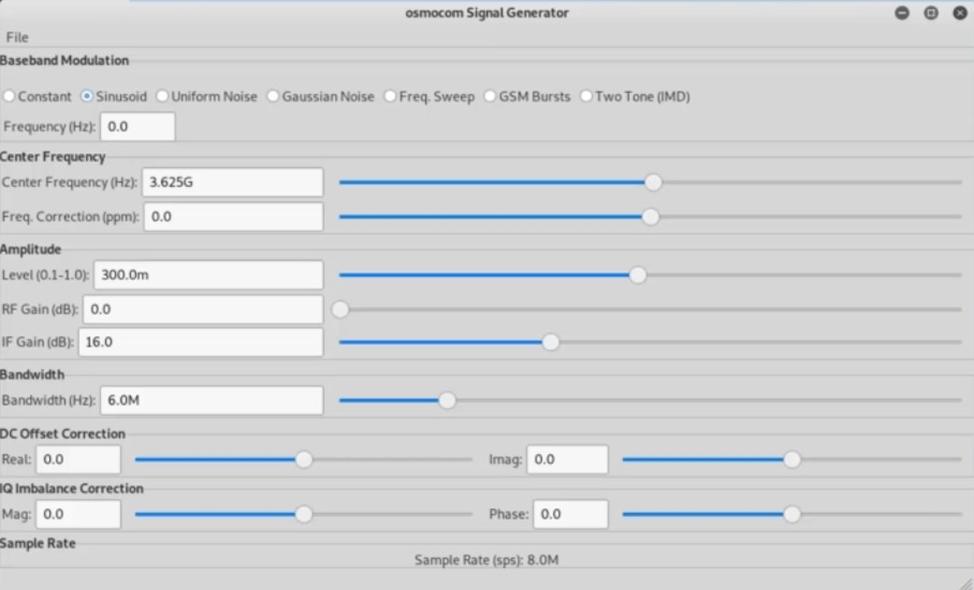
Now set frequency which we jamm
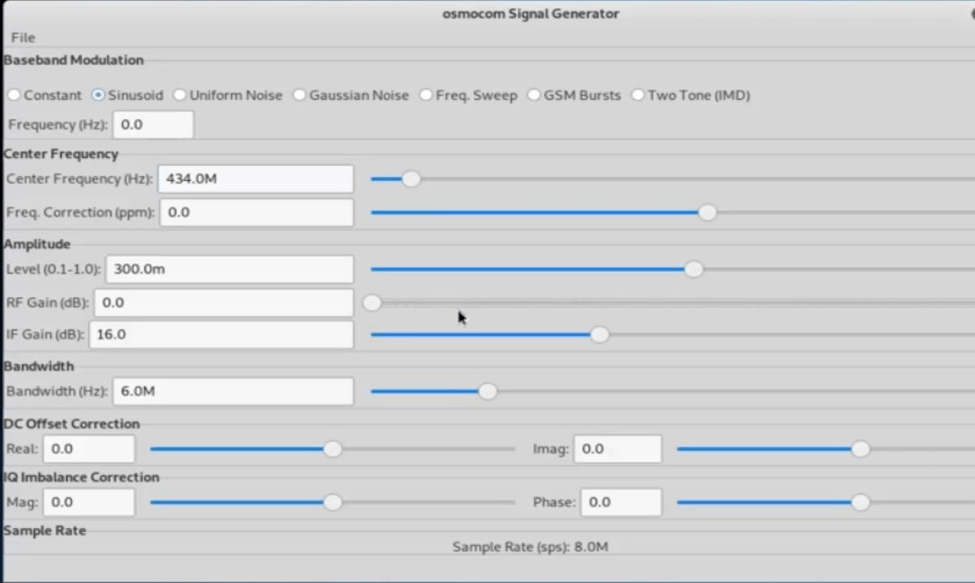
Now we can use this software in many ways,
We can make disturbances in signals in many ways
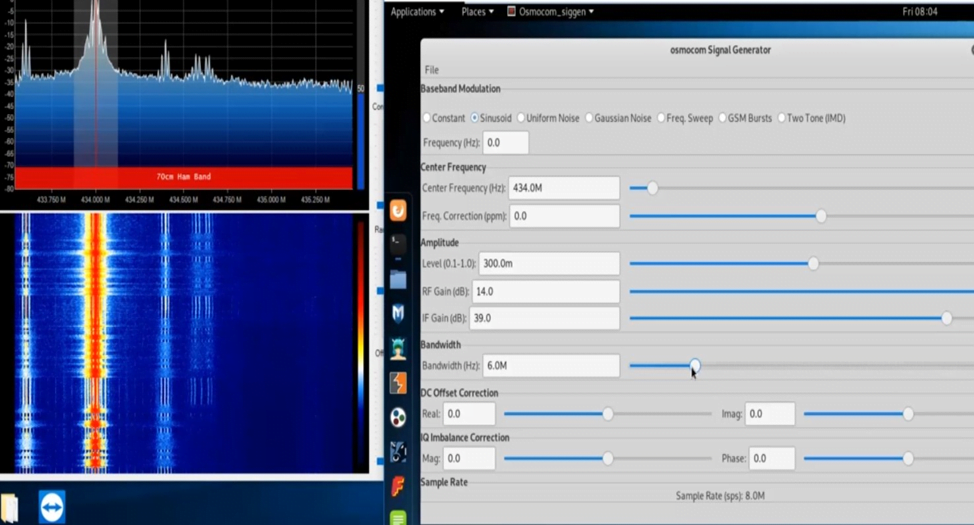
You see a little distortion in signals
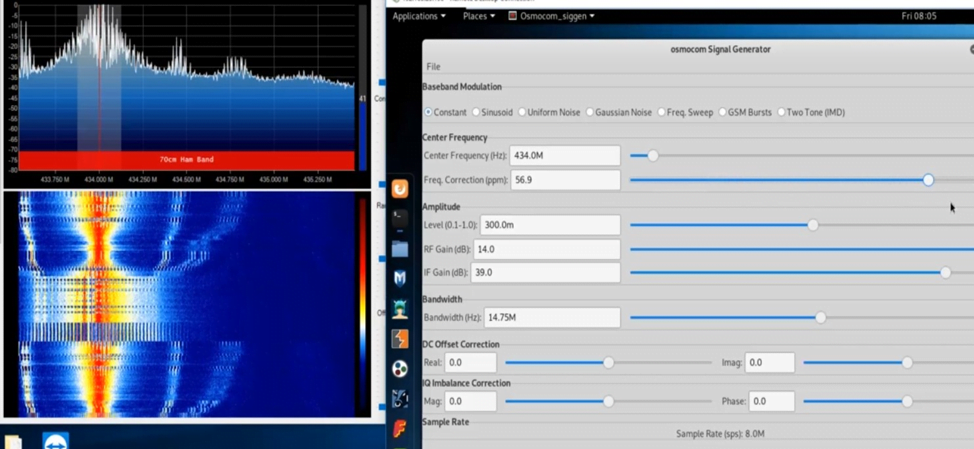
There are many methods to jamm signal in this software.
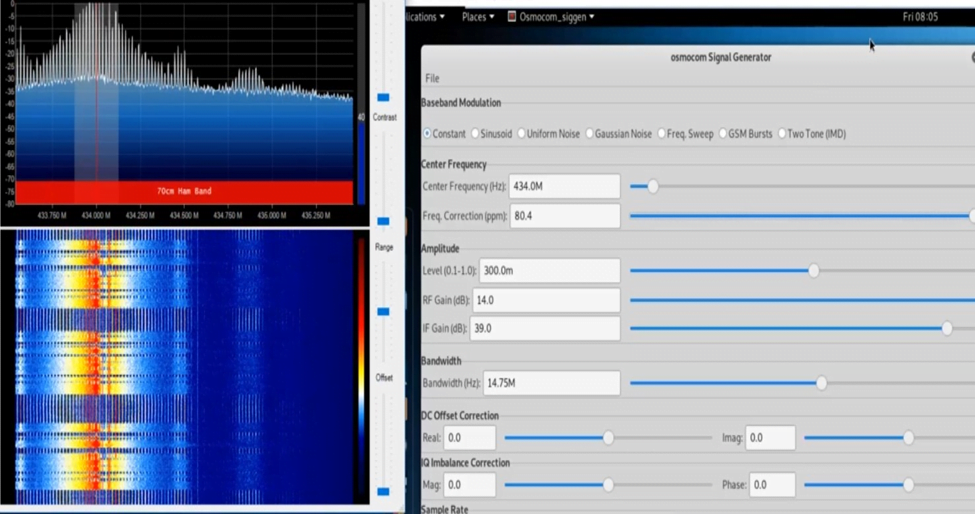
“So you see all distortion of signals in up pictures so that’s all our project is first we broadcast signals with raspberry and then we jamm these signals.”
CNC MACHINE.
CNC MACHINE.
Through a wide variety of CNC MACHINE
- service CNC MACHINE
Abstract:
This system is mainly based on two techniques, CNC machine and 3D printing. 2D plotter is used for drawing circuits on any surface like paper, cardboard as per the user requirement and conductive ink or marker is used as an object for drawing circuits. Conductive marker is placed in such a way that it can be moved in x and y direction using stepper motor and in up and down direction using servo motor. Arduino Uno or mega and CNC shield is used to drive motors. Benbox software is used to generate G-code and give input image of drawn circuit to the plotter. The research work is focused on a low cost and simple controlling system for 2D plotter machines to draw electronic circuit diagrams of PCBs on any surface.
I. INTRODUCTION
In last few years the production of electronic devices such as mobile phones, tablet, notebook, etc. has been increased tremendously. This technology revolution has been happened because of the large use of PCBs in every circuit. The operation of the electronic circuit is based on the flow of the electrical current through a desire paths from one point to another point. This path is drawn using the conductive marker placed on the 2D plotter.
There is also another method called photochemical method which uses ferric chloride compound to etch different layers of the board in order to clear the paths for the current, but in recent analysis it is found that the use of ferric chloride lead to significantly more risky for human health.
The implementation of this technique eliminates the human interaction with such compounds and replace the use of such hazardous chemical methods with a computerized mechanic system.
The working of 2D plotter is based on CNC machine and 3D printing where an object is moved with the help of two stepper motor in x and y direction as per the given input image. The input image is prepared with the help of express pcb or Autodesk eagle software. That image is converted into the numerical form of code known as g-code with the help of Benbox software which will give the instruction to the plotter to move the object from this point to that point in co-ordinates form as per layout. Here the object used is conductive marker as per our application.
II. SCHEME OF IMPLEMENTATION There are two systems implemented in this project.
A::
The first system is based on arduino UNO, BenBox software, Stepper motors, Servo motor and Conductive Marker.
The second system is based on arduino MEGA, L293D shield, Inkscape Software, Processing software, DVD driver stepper motors, Servo motor and Conductive Marker. It is shown in Fig.2.
- Input supply
Input supply is of 12 V for both CNC shield and L293D motor shield, which is used to drive motors and 5v supply is given to the arduino board.
- Arduino IDE
It is a software that gives software development tools for Arduino development boards. In this project we have to interface motors and check for serial communication using arduino IDE.
Arduino uno or mega platform is used in this systems which drives the motor with the help of CNC shid and L293D motor shield. The g-code instructions are given from the Benbox and processing software. Arduino UNO has Atmega328p and Mega has ATMEGA 2560 microcontroller. Technical features are shown in table.1 below.
- Please confirm that I have understood the task correctly. You would like me to rewrite the given text to make it clearer by correcting any spelling, grammar, and punctuation errors and improving its overall clarity and readability. Is that correct? Arduino IDE, Express PCB or Autodesk Eagle, Benbox.Autodesk Eagle is a software that is used to design the board layout of any circuit. An example of a
- 5V 1A power supply circuit.
- The G-code of an image is generated using Benbox software. It is only supported by the Windows operating system. It can configure the microcontroller. Speed, steps, and other parameters can be controlled using this software. The output from Autodesk Eagle which is a mirror image of the layout when imported uses its own default algorithm to find out the coordinates and generates a hex file.

G-code is the numeric code which tells the machine to go from a one position to the other specific position.
- Hardware used in this system: Components required to build this system are CNC shield, Arduino UNO, A4988 motor driver, DVD drive stepper motor and MG90s Servo motor.
Setup between Arduino UNO, motor driver and stepper motor

- A4988 motor driver is used to drive one stepper motor. It is placed on the CNC shield. It can operate on 5 to 36V supply voltage and upto 2A current.

It is a 16 pin Ic. Input is given to the STEP and DIR pin of the IC and output is taken from 1a, 1b, 2a &
2b for motor. Driver and its connections are shown in the Fig
- The motors used in this setup are stepper motors and are taken from the DVD drives. Two motors are required, one for x direction and other for y direction. the input supply given to this motor is 12V, given through a shield. The step angle is 18 degrees. Its holding torque is 25g.cm.[5]. The motor used is shown in the Fig.9.

- MG90s Servo motor is used for the movement in z direction that is for up and down movement of the conductive marker. It requires 5V supply voltage. It has 180 degrees step angle. Torque is 1.8kgf.cm..

Hardware setup of 2D plotter using Arduino UNO

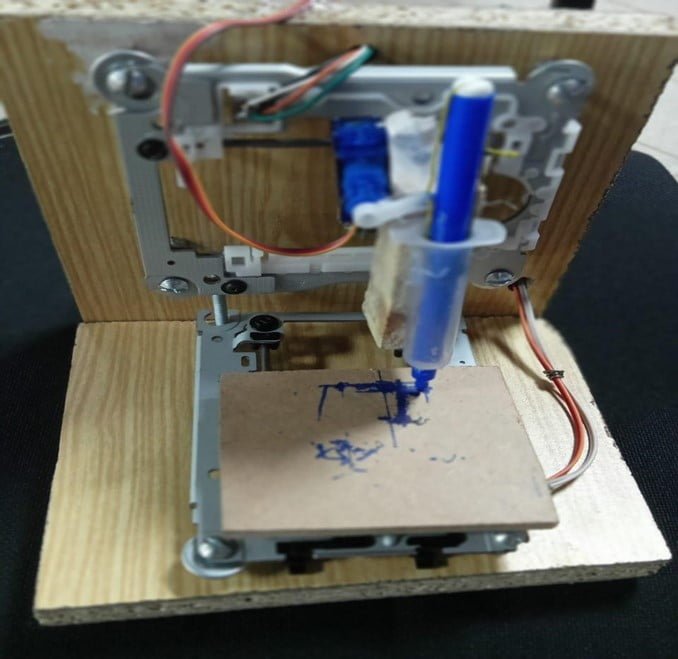
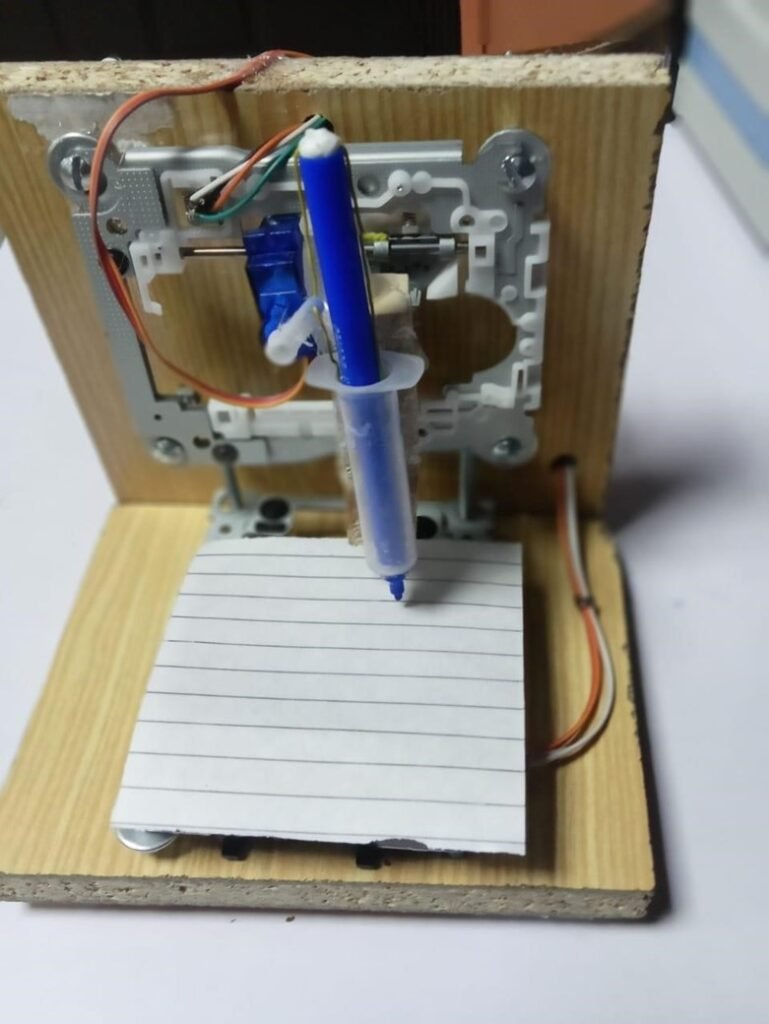
The system developed can draw a circuit using a conductive marker, which is a g-code of the image given to the Arduino Mega using processing software.
IV. CONCLUSION
This project can play a vital role in the Research and Development field, where we can print an idea of any circuit that comes to mind on paper or cardboard using conductive ink and check the different components working with the same circuit in a short period of time.
The main aim of this project is to reduce the bulkiness of PCB, which gives rise to the new technology of flexible electronics by enabling the printing of the circuits on surfaces like cardboard and photo papers. G-code is used to plot the location easily. The design of this project is to reduce error and increase accuracy & productivity. This project is helpful for students during their implementation of the project as far as cost and time are concerned.
The first system, which was based on Arduino UNO and CNC shield, was unable to draw images directly given in the g code form. It only draws the diagrams which are drawn in the Ben Box software. Thus, we go for another system, which is based on Arduino MEGA and L293D shield, which can draw any image given to the system in the form of g code.
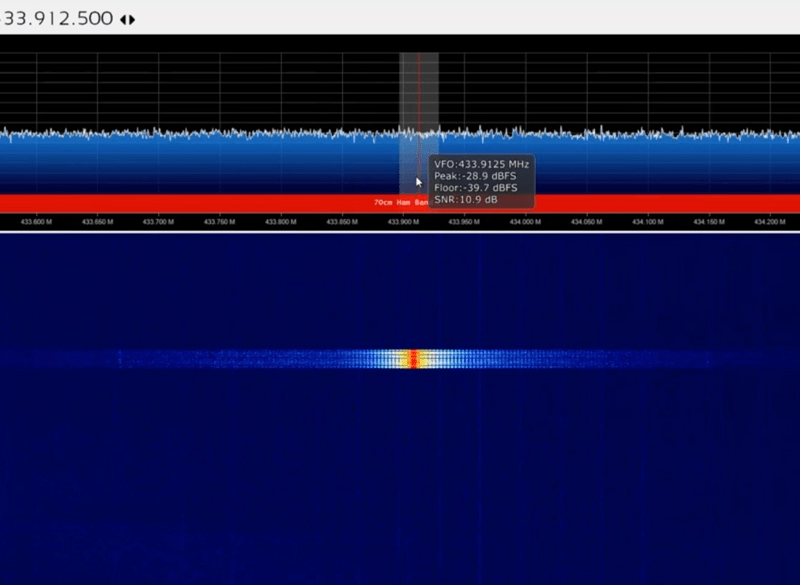
Hack 433 MHz Devices with a Raspberry and a RTL-SDR Dongle.
Hack 433 MHz Devices with a Raspberry and a RTL-SDR Dongle.
Through a wide variety of Hack 433 MHz Devices, We Hack 433 MHz Devices with a Raspberry and a RTL-SDR Dongle.
- Service Hack 433 MHz Devices
Hack 433 MHz Devices with a Raspberry and a RTL-SDR Dongle
Wireless things frequency is between 300MHz to 433MHz we find a frequency with the help of RTL-SDR Dongle
In this project we hack a Doorbell
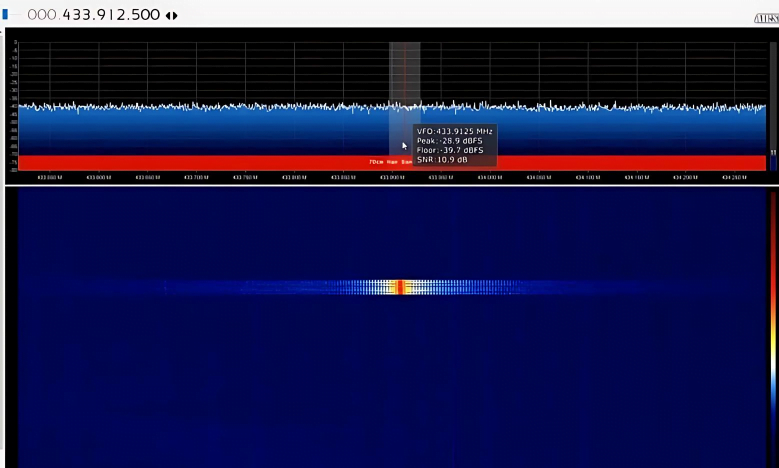
We get frequency with RTL-SDR Dongle on AIRSPY SDR software
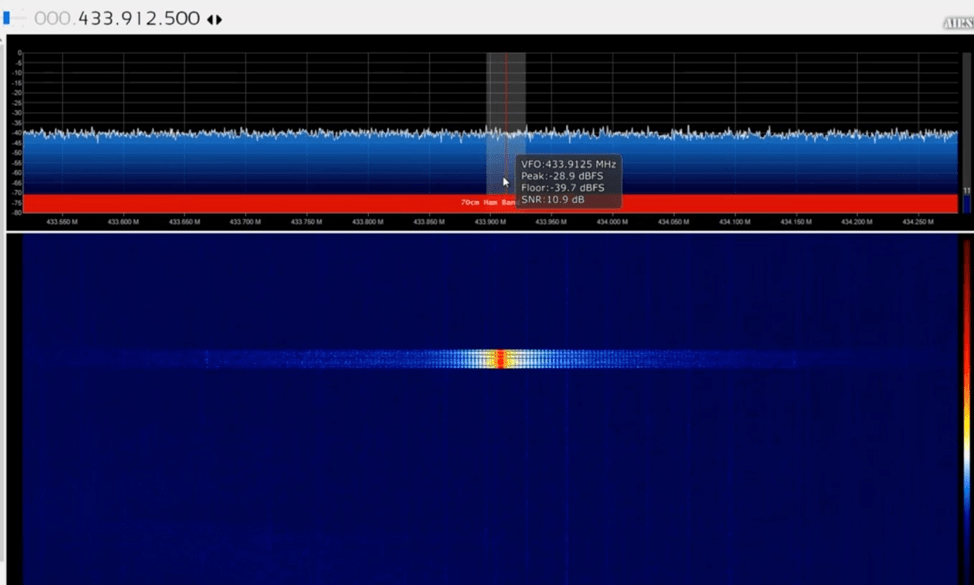
We get frequency of Doorbell at 433.912.500 we note this frequency where Doorbell rings
Then we connect our RTL-SDR Dongle with Raspberry

We connect RTL-SDR Dongle with raspberry pi to Do reply attack
We do reply attack using rpitx software in raspberry pi
We get this software from github
Source https://github.com/F5OEO/rpitx
Then we installed this software with these commands
git clone https://github.com/F5OEO/rpitx
cd rpitx
./install.sh
What kind of functions this software can perform

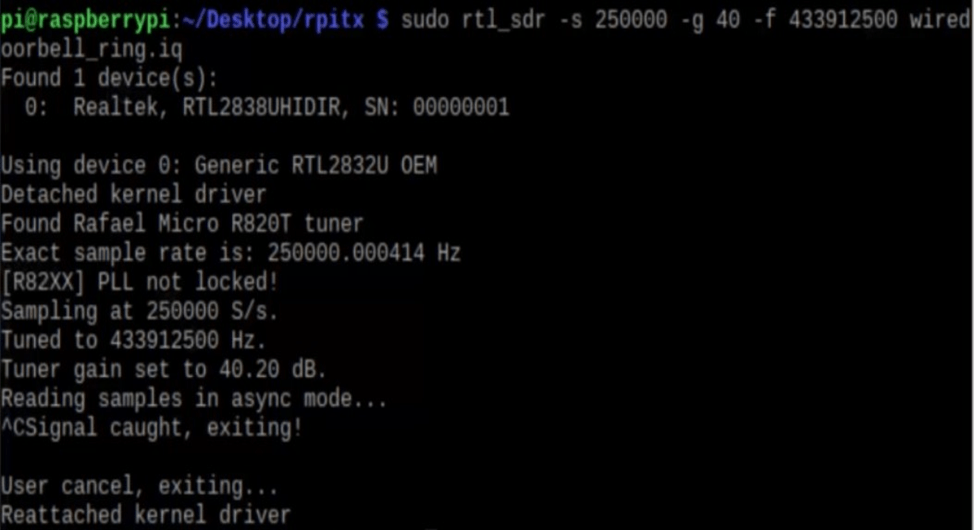
Now we know the frequency of the doorbell we execute the command to record the the frequency and then we reply that frequency
We use this command
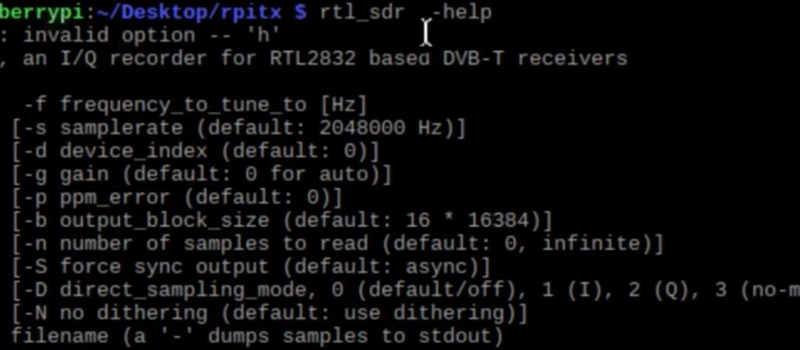
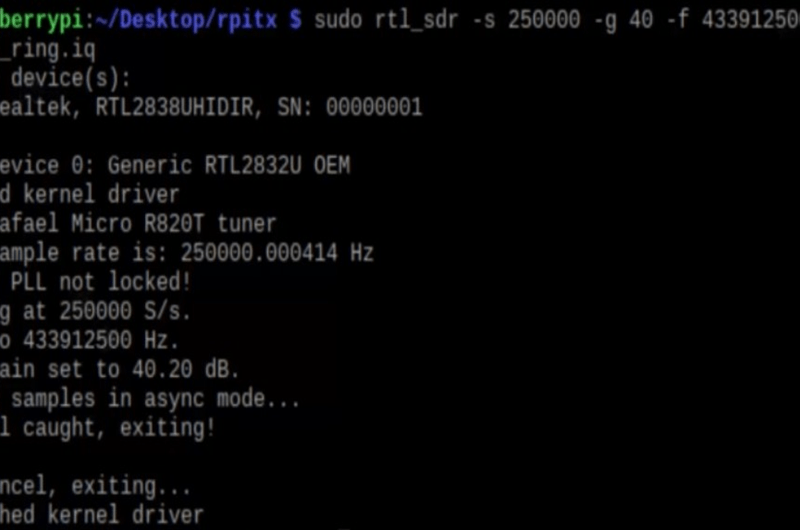
“ rtl_sdr -s 250000 -g 40 -f 433912500 wiredoorbell_ring.iq ”
rtl_sd : which device we use
-s 250000 : sample rate
-g 40 : gain
-f 433912500 : frequency
wiredoorbell_ring.iq : file name where records are.
recording frequency of doorbell
For reply attack we use ./sendiq command
What kind of functions this command can perform
Then for reply attack we use this command
“ ./sendiq -s 250000 -f 433912500 -t u8 -i wiredoorbellring.iq ”
-s 250000 sample rate
-f 433912500 frequency
-t u8 file formate
-i wiredoorbellring.iq recorded file
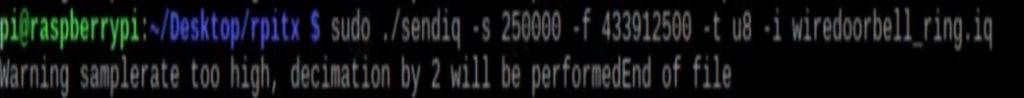
“Then our doorbell rings without button just with the help of this command only”
Pricing
My Pricing
Make Your Single Page
Elementor / WPBakery
$30.00
All the Lorem Ipsum generators on the Internet tend to repeat predefined chunks as necessary
1 Page with Elementor
Design Customization
Responsive Design
Content Upload
Design Customization
2 Plugins/Extensions
Multipage Elementor
Design Figma
MAintaine Design
Content Upload
Design With XD
8 Plugins/Extensions
ORDER NOW
2 Days Delivery
Unlimited Revission
Design Make this Page
Elementor / WPBakery
$50.00
All the Lorem Ipsum generators on the Internet tend to repeat predefined chunks as necessary
5 Page with Elementor
Design Customization
Responsive Design
Content Upload
Design Customization
5 Plugins/Extensions
Multipage Elementor
Design Figma
MAintaine Design
Content Upload
Design With XD
50 Plugins/Extensions
ORDER NOW
2 Days Delivery
Unlimited Revission
Customize Your Single Page
Elementor / WPBakery
$90.00
All the Lorem Ipsum generators on the Internet tend to repeat predefined chunks as necessary
10 Page with Elementor
Design Customization
Responsive Design
Content Upload
Design Customization
20 Plugins/Extensions
Multipage Elementor
Design Figma
MAintaine Design
Content Upload
Design With XD
100 Plugins/Extensions
ORDER NOW
2 Days Delivery
Unlimited Revission
Visit my blog and keep your feedback
My Blog
Contact
Contact With Me

Muhammad Ahsan
I am available for freelance work. Connect with me via mail.
Phone: +92 332 5058114
Email: ahsanaawan5911883@gmail.com
FIND WITH ME
[contact-form-7 id=”6″ title=”Contact form 1″]

Muhammad Ahsan
© 2024. All rights reserved by Muhammad Ahsan